Square is the popular start-up company that allows iPhone and Android users to process credit card transactions using their phone and a free credit card reader dongle that plugs into the phone’s headphone jack.
VeriFone, a leader in credit card transaction technology has a similar product (PayWare Mobile app), but Square’s minimalistic approach to its transactions (no merchant account needed, no credit check, AND a free credit card reader) has proved to be some serious competition for Verifone. I’m not sure if Verifone is generally concerned with the financial security of the consumers, or this is an outright attempt to squash the competition, but VeriFone’s CEO has just released an Open Letter, demonstration video, AND a free fake Square app that allegedly identifies and demonstrates a serious hole in Square’s ability to encrypt credit card information when swiping it through the free credit card reader.
http://www.youtube.com/watch?v=ObGQxSuORy0&feature=player_embedded
Whatever the reasoning, VeriFone is serious about this latest development and has called out Square and notified its credit card processing partners (Visa, MasterCard, American Express, and JP Morgan Chase). The Fake Square App released by Verifone can be downloaded by ANYONE to test this flaw for themselves.
To back VeriFone, if this is true, the possibilities for ANYONE with the Square reader, a decent card skimming application, and your trust can have your credit card information within a matter of seconds. THAT’S A PROBLEM, and could mean curtains for Square, let alone any legal implications if this particular issue goes mainstream.
To back Square, if VeriFone REALLY cared about the consumer’s credit card security, and not its revenue, would it have just given would-be crooks the keys, complete with an instruction manual and tutorial video to steal our credit card information? Additionally, card skimming is not a new trick and companies like VeriFone have been fighting for years, so it’s not solely a Square issue. In the end, it all boils down to customer common sense as it relates to who you hand over your credit card to.
/Rant off
Nonetheless, the implications are serious enough that it needs to be addressed, and so far, mums the word from Square. Hopefully the company’s representatives will respond and restore its customer’s sense of trust and security and continue to offer its products and services to individuals and small businesses who want accept credit card payments, while offering competition to larger credit card processing companies. Competition is always good for the consumer.
[via: Engadget]
 Dropbox, Box, Microsoft SkyDrive, SugarSync, and Google Drive have been getting all the consumer cloud storage love as of late. The services are uber-popular, but may not be the best option for the enterprise due to the simple fact sensitive documents/files stop being sensitive once they are downloaded onto personal mobile devices. Nexus by ionGrid is a solution that lets users access and modify files from an iPad while they file stay protected by company IT policy.
Dropbox, Box, Microsoft SkyDrive, SugarSync, and Google Drive have been getting all the consumer cloud storage love as of late. The services are uber-popular, but may not be the best option for the enterprise due to the simple fact sensitive documents/files stop being sensitive once they are downloaded onto personal mobile devices. Nexus by ionGrid is a solution that lets users access and modify files from an iPad while they file stay protected by company IT policy.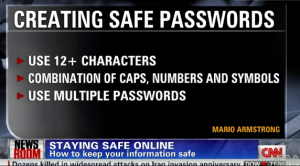 And choose a good password! I can’t say this enough, but if you can’t remember strong passwords and use different, strong passwords for every important account you have (email, banking, etc.) then you need to look into a password management system. I’m not going to do your homework for you, but services like
And choose a good password! I can’t say this enough, but if you can’t remember strong passwords and use different, strong passwords for every important account you have (email, banking, etc.) then you need to look into a password management system. I’m not going to do your homework for you, but services like